Install WPScan WordPress Security Scanner on Ubuntu 20.04 LTS
29/09/2021 By RuneLite
Commands to install WPscan WordPress security scanner on Ubuntu 20.04 or 18.04 Linux distos to find plugin or themes vulnerabilities & other security issues.
WPScan WordPress Security Scanner is a free-to-use tool available to install for Linux & Windows systems. It lets users check the security issues related to some WordPress installed blog or website. This means, the user can scan any website based on WordPress to find out various issues such as core files, plugins, and themes vulnerabilities; Weak passwords, HTTPS enabled or not, Header items; including a check for debug.log files, wp-config.php backup files, XML-RPC is enabled, code repository files, default secret keys, exported database files and more... However, to get the vulnerabilities in the result, we need to add the WPscan API key available free to generate and provides 25 scans daily.
Furthermore, Wpscan is also available as a plugin to directly install on the WordPress backend and the users can operate it via its GUI Dashboard. In case you don’t want to use the WPscan plugin then the CLI tool can be used.
Contents
Step to Install WPScan on Ubuntu 20.04/18.04 LTS
1. Run system update
2. Install Ruby on Ubuntu 20.04 LTS
3. Command to install WPScan on Ubuntu
4. Check out the version
5. WPscan Commands
6. Scan WordPress Sites
7. Get WPScan Token API Key
8. Detection modes
9. List all installed Plugins & Themes and scan for vulnerabilities
10 Run WPscan to bypass WAF
Step to Install WPScan on Ubuntu 20.04/18.04 LTS
Let’s see the commands to install this WordPress Vulnerability Scanner (WPscan) on Ubuntu, Debian, Kali Linux, Linux Mint, or similar other operating systems.
1. Run system update
The first thing that should be performed before installing some application or tool is running of the system update command-
sudo apt update
2. Install Ruby on Ubuntu 20.04 LTS
Wpscan is available to install from RubyGems, thus let’s install Ruby and other required dependencies on our Ubuntu-
sudo apt install ruby-full
3. Command to install WPScan on Ubuntu
Finally, use Ruby’s gem command to download and install the WPscan packages on your system.
sudo gem install wpscan
4. Check out the version
Once the installation is completed, let’s check its version-
wpscan --version
5. WPscan Commands
To know the various commands and flags that can be used with Wpscan, open the help section.
wpscan -h
Usage: wpscan [options]--url URL The URL of the blog to scan Allowed Protocols: http, https Default Protocol if none provided: http This option is mandatory unless update or help or hh or version is/are supplied-h, --help Display the simple help and exit--hh Display the full help and exit--version Display the version and exit-v, --verbose Verbose mode--[no-]banner Whether or not to display the banner Default: true-o, --output FILE Output to FILE-f, --format FORMAT Output results in the format supplied Available choices: cli-no-colour, cli-no-color, json, cli--detection-mode MODE Default: mixed Available choices: mixed, passive, aggressive--user-agent, --ua VALUE--random-user-agent,--rua Use a random user-agent for each scan--http-auth login:password-t, --max-threads VALUE The max threads to use Default: 5--throttle MilliSeconds Milliseconds to wait before doing another web request. If used, the max threads will be set to 1.--request-timeout SECONDS The request timeout in seconds Default: 60--connect-timeout SECONDS The connection timeout in seconds Default: 30--disable-tls-checks Disables SSL/TLS certificate verification, and downgrade to TLS1.0+ (requires cURL 7.66 for the latter)--proxy protocol://IP:port Supported protocols depend on the cURL installed--proxy-auth login:password--cookie-string COOKIE Cookie string to use in requests, ....more
6. Scan WordPress Sites
Now, if you want to use this command-line tool to scan some WordPress website to find security issues and other details run the following syntax-
wpscan --url http://your-website.com
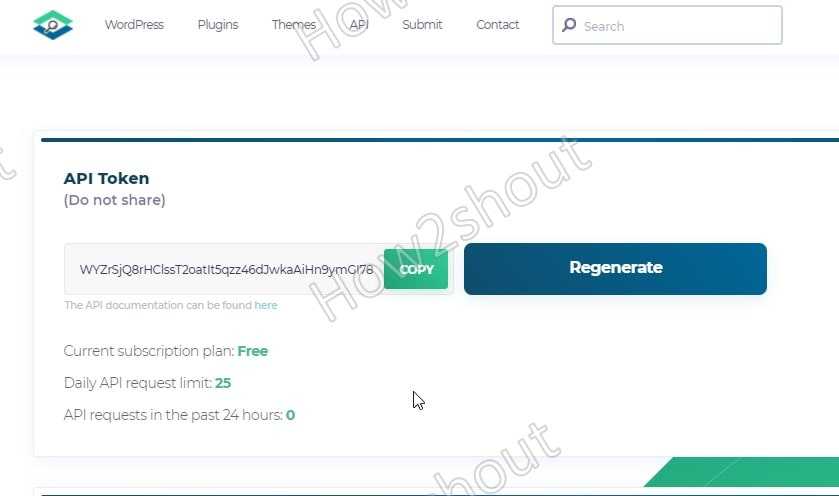
7. Get WPScan Token API Key
By default, this security tool will not provide Vulnerabilities in the result, and to get that we have to generate an API key. Go to the official website and select the free plan to register.
Copy the API key and use it in the following way with the command-
wpscan --url your-website.com --api-token your-api-key
Note: Replace your-api-key text in the above command with the one which you have generated.
8. Detection modes
Wpscan offers three detection modes, they are passive, aggressive, and mixed. In Passive Mode, the tool will send few requests to the server and only scan to find out common security issues for the Homepage of a website. It is good to use if you think the server won’t be able to handle a large pool of requests.
Coming to Aggressive mode, in this, the intrusive scan run by WPscan will be more powerful and will send hundreds of requests to the server to find out vulnerabilities, if any, in all plugins of WordPress.
Whereas, mixed which is the default on the WPScan tool is a combination of aggressive and passive mode to provide a balanced scan.
So, if you want to override the default Mixed by any of the other two, use
--detection-mode
option in the command-
For example:
wpscan --url your-website.com --detection-mode aggressive --api-token your-api-key
9. List all installed Plugins & Themes and scan for vulnerabilities
To enumerates various items of WordPress, we can use the options given below with
-e
flag.
vp ----(Vulnerable plugins)ap ----(All plugins)p ----(Popular plugins)vt ----(Vulnerable themes)at ----(All themes)t ----(Popular themes)tt ----(Timthumbs)cb ----(Config backups)dbe ----(Db exports)u ----(User IDs range. e.g: u1-5)m ----(Media IDs range. e.g m1-15)
For example, we want to List all plugins with known vulnerabilities, then we use the vp option given in the above list along with -e flag detection mode
wpscan --url your-website.com -e vp --detection-mode mixed --api-token your-api-key
10 Run WPscan to bypass WAF
To run the scan in hidden mode so that the Web application firewall couldn’t detect Wpscan, one can try
--random-user-agent
and
--stealthy
options.
This was a quick tutorial & introduction to the WPscan installation on Ubuntu 20.04 and other similar Linux distros. To know more about this tool you can check out its GitHub page/documentation.